Web Smarts - Business Savvy
We’ve been building websites since 1998
We are trusted advisors to Over 50 Active Clients within several industries including associations and nonprofits, healthcare, financial services, retail, B2B and more.

We Are
Trusted
Partners
After we deliver a quality website on time and within your budget, we will be there for when it really counts. We will be proactive, consultative and strategic after we launch your website.

We Are
Integration
Experts
We’ve integrated with virtually every AMS system on the market as well as most LMS, publication, advocacy and career center applications. Our company was founded on custom development.

We build websites that are easy to edit, manage and design using the best content management system on the market, Sitefinity CMS.
We Provide A Full Spectrum Of Services
Our Clients Are Our Partners....
John Wurm

The team at Vanguard helped us think about our digital presence from the perspective and needs of our users, while holding true to the values our organization espouses.
Connect With Us
Improve Your Webcopy

The
Vanguard View
Technology articles about one topic from the perspective of Leadership, Marketing and IT professionals .
What is Encryption?
You may have heard the word “Encryption” before, but do you know its purpose and where it came from? Encryption is manipulating a message so that it can be viewed by all, but only understood by the sender and the intended recipient. Cryptography, the art/study of encryption, is much older than any computer, dating back at least to 1900BC according to Wikipedia.
Decoding History
Before the age of computers, a cipher, or the secret key to decoding the message, could be anything. To name some famous examples, one of the solved Beale cyphers uses the Declaration of Independence as its key. In the movie a Christmas Story, Ralph uses a secret decoder pin to decode Annie’s secret message. You may also remember the “secret decoder rings” that were once prizes in cereal boxes. These rings encrypted a message using a substitution cipher in a circular disk. A number would represent a letter, and a “key” was needed in order for the message to be decoded. By turning the dial on the ring, one could follow the key to crack the code letter-by-letter. Many came in pairs, so friends could send each other secret messages. You can still get these today.

Image taken from Lee Valley Toys
A more serious example was Germany using Enigma machines during WWII to encrypt and decrypt messages.
Frequency Analysis
Encryption only works if it cannot be decrypted by anyone who does not possess the key. In early cryptography a common way to break a substitution cipher was frequency analysis. In a substitution cipher each character is replaced with another making the message unreadable, like the decoder ring example above. With frequency analysis, we start by making an assumption about the language the original message was in. Then, we count each character to see how often it appears.
If we think the message is in English, we assume the most common letter in our message was switched with an “E.” Next, we replace the next most frequent letter in our message with the next most frequent letter in English. This goes on and adjustments are made until you can read the message. After only a few replacements, it may start to feel like playing wheel of fortune.
To avoid this from happing, each block of the message should not be encrypted individually. One way around frequency analysis is to employ cipher block chaining, altering the block being encrypted with what came before it using something like XOR, also known as “Exclusive Or”. Yes, this is the same principal as the Blockchain distributed ledgers used in cryptocurrency. To break this down a bit further, here is an example of XOR in binary.
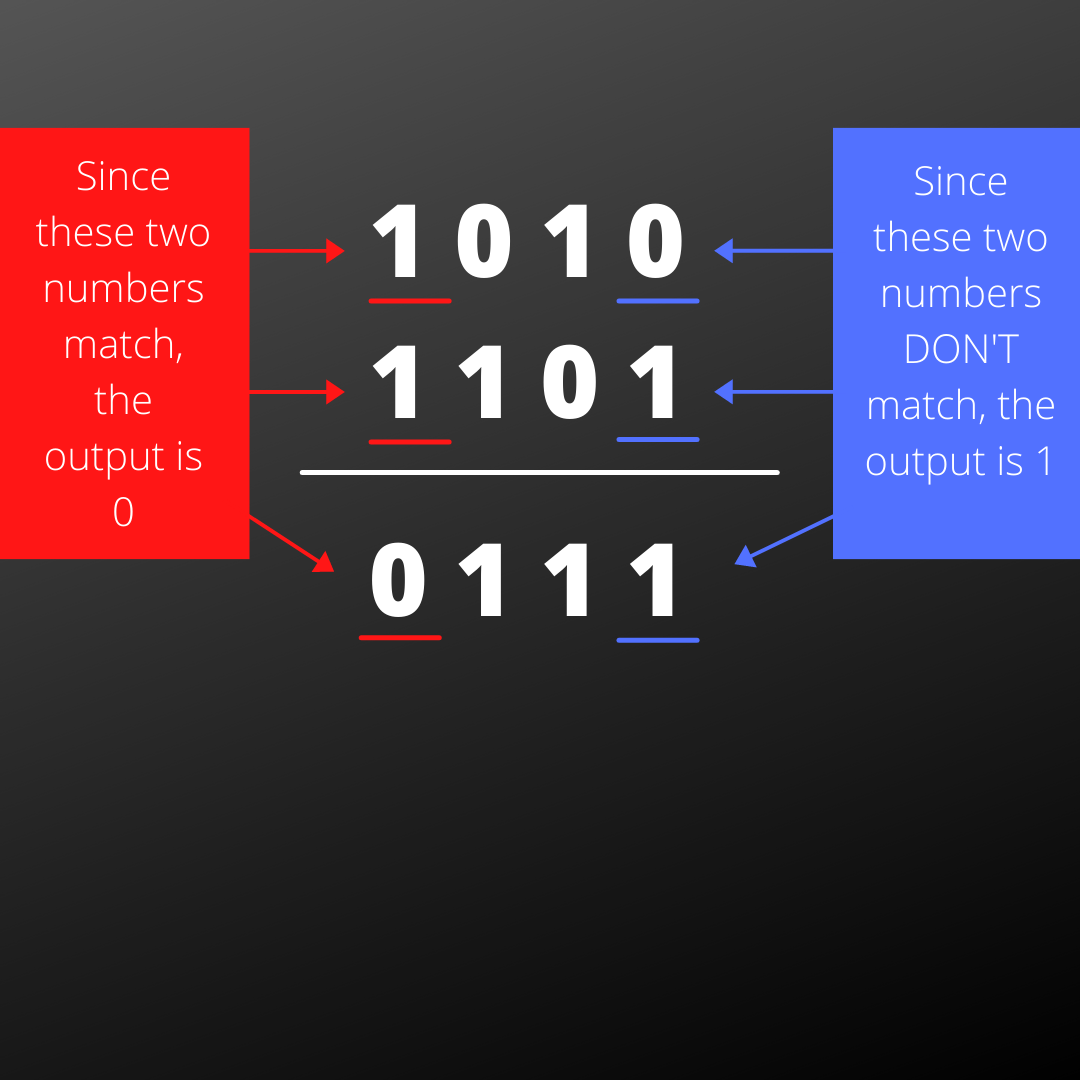
As you can see from the graphic, you are given two sets of binary numbers. If you line the numbers up and they match, the output is zero. If they don’t, the output is one. Now, let’s just say the number you are given is the output and the second set of binary numbers. By using the output and the second set, you can use XOR to find the first set of binary numbers.
A college professor once joked, “All cryptographers do any more is XOR.” XOR is a logical operation a computer can execute with 2 values. If the resulting value is put through the same operation again with one of the original values, the other original value is revealed.
Today’s Encryption
In the modern era, cipher keys are generated by computers.
Symmetric-key encryption is shared key encryption. It is fast, efficient, and common. Symmetric cyphers come in two flavors: stream ciphers and block ciphers. Stream ciphers use on a somewhat random key generated by an algorithm to match the length of the message to be encrypted.
For the purpose of this article, we will focus on the more common block cipher. Block ciphers have a fixed key size and use cipher block changing to encrypt and decrypt blocks of data.
Public Key Encryption
Whitfield Diffie and Martin Hellman invented Public Key encryption, and their algorithm is used for key exchange.
To facilitate your use of encryption with ease, the internet relies on public key encryption and hashes. Public-Key encryption generates a pair of keys that complement each other. Each key can be used to encrypt or decrypt a message as long as it was done so by the corresponding “key”. This is often called public/private key pairs as one can verify the authenticity of a message by making one key public for all to see and keeping the other private. If the private key of the pair is able to successfully decrypt a message using the public key (or vice versa), one knows that the message was valid.
These two keys unlock each other. If a hacker got access to the encrypted message, they would still not have access to it, as the original sender and the intended recipient are the only ones with that key to authenticate. This is how SSL (Secure Sockets Layer) also known as TLS (Transport Layer Security) works.
Hashing
Hashing is an algorithm that allows us to create a digital signature. Unlike symmetric-key encryption which produces a key pair and the messages encrypted by one key can be decrypted by the other, hashing is one-way, meaning you should not be able to retrieve the input message from the output. Hashing results should also be unique. While the same input entered multiple times should produce the same result, no other input should produce that same result. In encryption, hashing guarantees the message was not tampered with in transit. Hashing is also pivotal in authentication as a mechanism to protect passwords from being leaked, even when the data is compromised.
Because of this feature, hashing is often used to protect passwords. For example, the password of “kUr4@sqU7” might be ran through a hashing algorithm and end up being “ejkbnco76”. We store the hashed value of the password. The next time the user types in that password, it is hashed again, and we get the same output. If the outputs of the stored hashed password and the recently hashed password match, we know that the original password must have been the same in both instances. This is a benefit because if the location where the hashed passwords are stored is ever compromised, the attacker does not know the passwords of the users.
An article from GCN.com by William Jackson explains how hashing works:
“A user enters a password and an ID in a browser and sends it (preferably over a secure link) to the authentication server. The server uses the ID to look up the associated message digest. The password submitted by the user is then hashed with the same algorithm, and if the resulting message digest matches the one stored on the server, it is authenticated.
In this process the server does not store or need to see plain-text passwords. Stealing hashed files does the attacker little good because the attacker cannot reverse the hashing process.”
Cryptography has certainly become more complex since its inception. If you would like to learn more about how encryption is used, and how we keep websites safe, please reach out to your Vanguard Client Manager today.
Vanguard Tips & Tricks
We provide helpful hints you never knew you needed for our clients. Check out "Vanguard Tips & Tricks" to learn quick and simple hacks to make managing your website easier than ever.
What is Encryption?
You may have heard the word “Encryption” before, but do you know its purpose and where it came from? Encryption is manipulating a message so that it can be viewed by all, but only understood by the sender and the intended recipient. Cryptography, the art/study of encryption, is much older than any computer, dating back at least to 1900BC according to Wikipedia.
Decoding History
Before the age of computers, a cipher, or the secret key to decoding the message, could be anything. To name some famous examples, one of the solved Beale cyphers uses the Declaration of Independence as its key. In the movie a Christmas Story, Ralph uses a secret decoder pin to decode Annie’s secret message. You may also remember the “secret decoder rings” that were once prizes in cereal boxes. These rings encrypted a message using a substitution cipher in a circular disk. A number would represent a letter, and a “key” was needed in order for the message to be decoded. By turning the dial on the ring, one could follow the key to crack the code letter-by-letter. Many came in pairs, so friends could send each other secret messages. You can still get these today.

Image taken from Lee Valley Toys
A more serious example was Germany using Enigma machines during WWII to encrypt and decrypt messages.
Frequency Analysis
Encryption only works if it cannot be decrypted by anyone who does not possess the key. In early cryptography a common way to break a substitution cipher was frequency analysis. In a substitution cipher each character is replaced with another making the message unreadable, like the decoder ring example above. With frequency analysis, we start by making an assumption about the language the original message was in. Then, we count each character to see how often it appears.
If we think the message is in English, we assume the most common letter in our message was switched with an “E.” Next, we replace the next most frequent letter in our message with the next most frequent letter in English. This goes on and adjustments are made until you can read the message. After only a few replacements, it may start to feel like playing wheel of fortune.
To avoid this from happing, each block of the message should not be encrypted individually. One way around frequency analysis is to employ cipher block chaining, altering the block being encrypted with what came before it using something like XOR, also known as “Exclusive Or”. Yes, this is the same principal as the Blockchain distributed ledgers used in cryptocurrency. To break this down a bit further, here is an example of XOR in binary.

As you can see from the graphic, you are given two sets of binary numbers. If you line the numbers up and they match, the output is zero. If they don’t, the output is one. Now, let’s just say the number you are given is the output and the second set of binary numbers. By using the output and the second set, you can use XOR to find the first set of binary numbers.
A college professor once joked, “All cryptographers do any more is XOR.” XOR is a logical operation a computer can execute with 2 values. If the resulting value is put through the same operation again with one of the original values, the other original value is revealed.
Today’s Encryption
In the modern era, cipher keys are generated by computers.
Symmetric-key encryption is shared key encryption. It is fast, efficient, and common. Symmetric cyphers come in two flavors: stream ciphers and block ciphers. Stream ciphers use on a somewhat random key generated by an algorithm to match the length of the message to be encrypted.
For the purpose of this article, we will focus on the more common block cipher. Block ciphers have a fixed key size and use cipher block changing to encrypt and decrypt blocks of data.
Public Key Encryption
Whitfield Diffie and Martin Hellman invented Public Key encryption, and their algorithm is used for key exchange.
To facilitate your use of encryption with ease, the internet relies on public key encryption and hashes. Public-Key encryption generates a pair of keys that complement each other. Each key can be used to encrypt or decrypt a message as long as it was done so by the corresponding “key”. This is often called public/private key pairs as one can verify the authenticity of a message by making one key public for all to see and keeping the other private. If the private key of the pair is able to successfully decrypt a message using the public key (or vice versa), one knows that the message was valid.
These two keys unlock each other. If a hacker got access to the encrypted message, they would still not have access to it, as the original sender and the intended recipient are the only ones with that key to authenticate. This is how SSL (Secure Sockets Layer) also known as TLS (Transport Layer Security) works.
Hashing
Hashing is an algorithm that allows us to create a digital signature. Unlike symmetric-key encryption which produces a key pair and the messages encrypted by one key can be decrypted by the other, hashing is one-way, meaning you should not be able to retrieve the input message from the output. Hashing results should also be unique. While the same input entered multiple times should produce the same result, no other input should produce that same result. In encryption, hashing guarantees the message was not tampered with in transit. Hashing is also pivotal in authentication as a mechanism to protect passwords from being leaked, even when the data is compromised.
Because of this feature, hashing is often used to protect passwords. For example, the password of “kUr4@sqU7” might be ran through a hashing algorithm and end up being “ejkbnco76”. We store the hashed value of the password. The next time the user types in that password, it is hashed again, and we get the same output. If the outputs of the stored hashed password and the recently hashed password match, we know that the original password must have been the same in both instances. This is a benefit because if the location where the hashed passwords are stored is ever compromised, the attacker does not know the passwords of the users.
An article from GCN.com by William Jackson explains how hashing works:
“A user enters a password and an ID in a browser and sends it (preferably over a secure link) to the authentication server. The server uses the ID to look up the associated message digest. The password submitted by the user is then hashed with the same algorithm, and if the resulting message digest matches the one stored on the server, it is authenticated.
In this process the server does not store or need to see plain-text passwords. Stealing hashed files does the attacker little good because the attacker cannot reverse the hashing process.”
Cryptography has certainly become more complex since its inception. If you would like to learn more about how encryption is used, and how we keep websites safe, please reach out to your Vanguard Client Manager today.
Case Studies
Vanguard conducts thorough preliminary investigative work to ensure your website is built to cater specifically to your target audience and meet your organization’s goals. Check out some of the case studies on some of our most recent client success stories.
What Can Vanguard Do For You?
As your organization grows and evolves, your website should as well. Whether you are looking to generate more traffic, implement custom functionality, mobile compatibility, integrate your systems, or give your site a complete redesign, Vanguard Technology is your go-to web partner. Reach out to us with your current concerns with your website, and our experts will happily provide a solution.










Leave a commentOrder by
Newest on top Oldest on top