Web Smarts - Business Savvy
We’ve been building websites since 1998
We are trusted advisors to Over 50 Active Clients within several industries including associations and nonprofits, healthcare, financial services, retail, B2B and more.

We Are
Trusted
Partners
After we deliver a quality website on time and within your budget, we will be there for when it really counts. We will be proactive, consultative and strategic after we launch your website.

We Are
Integration
Experts
We’ve integrated with virtually every AMS system on the market as well as most LMS, publication, advocacy and career center applications. Our company was founded on custom development.

We build websites that are easy to edit, manage and design using the best content management system on the market, Sitefinity CMS.
We Provide A Full Spectrum Of Services
Our Clients Are Our Partners....
John Wurm

The team at Vanguard helped us think about our digital presence from the perspective and needs of our users, while holding true to the values our organization espouses.
Connect With Us
Improve Your Webcopy

The
Vanguard View
Technology articles about one topic from the perspective of Leadership, Marketing and IT professionals .
Phishing for Grandma
My Grandma is joining the 21st century. She has a laptop, smartphone, and even a Facebook profile. Taking that leap was big, but she is taking it in strides and becoming more connected. However, her understanding of how this technology works is limited, and therefore makes her vulnerable to the more malicious side of the internet. Grandma has been hacked, attacked with ransomware,1 and started to lose faith in her choice to become more connected online. Therefore, this article is to help you (and your Grandma) understand what a Phishing attempt/attack is, identify it as such, and avoid giving away your sensitive information.
What is Phishing?
Put your tackle box and favorite rod away, were not going fishing… for fish. Instead, phishing is angler’s equivalent for hunting down information. A fisherman is chasing after fish and uses bait to tempt the fish onto their line. With phishing, the fisherman (phisherman?) is after your personal information and is using some sort of communication that seems legitimate as their bait. Put another way, phishing is one’s attempt to get information by posing as somebody or something else. For example, you receive an email from what you think is your bank saying that your online banking username and password have expired and need to be updated. You click on the link and update your information. However, when you visit your bank’s website later that day, you noticed your credentials have not been updated. You unknowingly gave away your login information to a stranger!
Phishing Mediums
While most phishing attempts are made over email, any method of communication can be exploited for the purposes of phishing information. One common theme of all phishing attempts is continued anonymity of the person phishing for information. If you can trace back where the attacker is, it would be much easier to rectify any wrongs committed. Therefore, many phishing attacks use temporary email domains or exploit a hacked website as a base of their attack.
Unfortunately, Grandma fell victim to a phishing attack by phone a couple of times. In one such instance, someone claiming they were from Microsoft, said that they detected a virus on her computer. In the course of two hours of speaking with Grandma this person was able to get her to provide them with the information necessary to access her computer remotely (using the same software I use to assist her). It was only after they had access did she become suspicious and call me for help. Unfortunately, the damage was done, and the attacker installed rudimentary ransomware1 onto her computer. We traced the phone number to an offshore “IT Support” company who, for a monthly subscription, will clean up any viruses on (and unlock any ransomware that they installed onto) your computer. Luckily, we were able to recover her files through other means, and the real loser in the scenario was the attacker who had to play the role of “tech support” to Grandma for over two hours.
How to spot
Phone calls
- Ask the caller for their name and position. Look up the support line for company they claim to be with. Hang up with the person who called you and attempt to call them back on the number you found. Do not trust any phone numbers that they provide you.
Websites
- Check the URL address of the website you are visiting for misspellings. If you are unsure, search for the website using your favorite search engine. Phishing attempts often involve buying a domain name that is similar to the real domain you are trying to visit in hopes that you don’t notice the change.
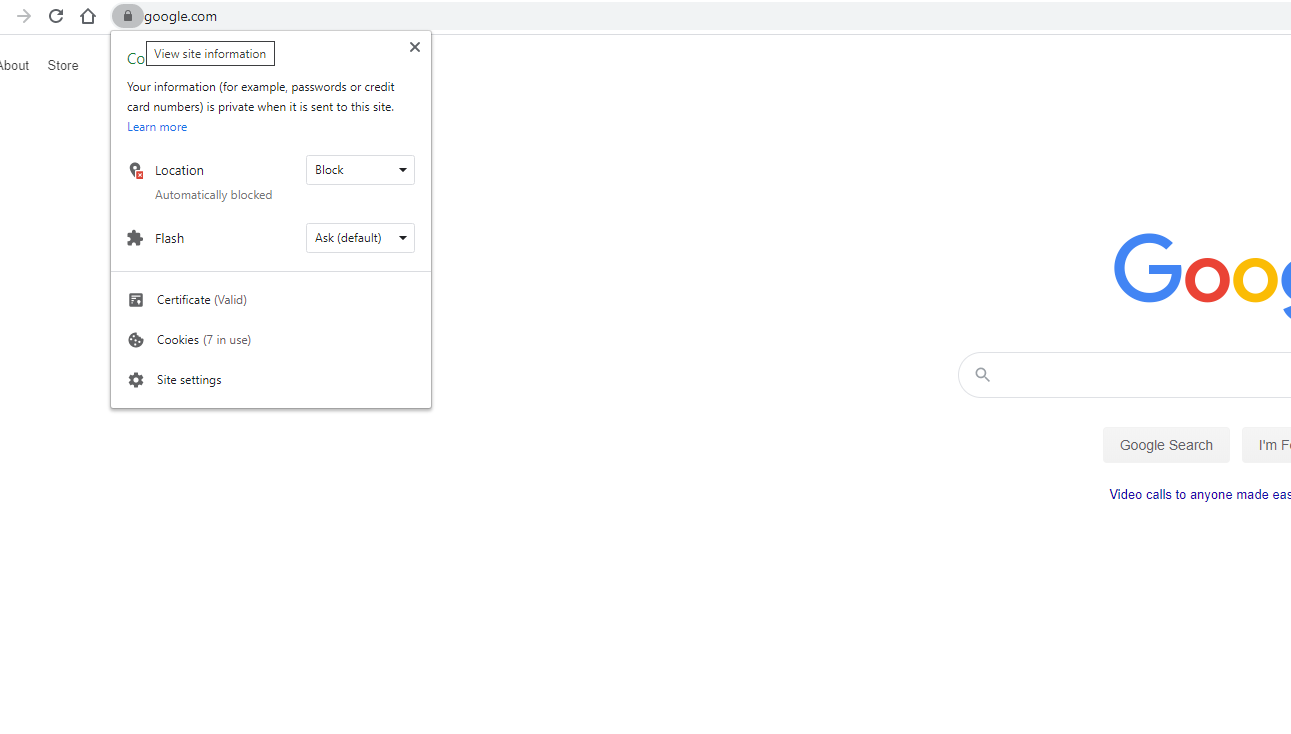
- Make sure your connection with the website is private and encrypted. Look in the upper left-corner of the URL bar for a lock icon. If your browser ever warns you that a website’s “Certificate is Self-Signed”, do not trust the website.
Emails
- Check the email address that sent you the message. This may not be the name of the individual that sent you the email. Phishing attempts often will use a friend’s name to make you think it is your friend who sent you an email. While they can spoof the name, it is much harder to spoof the email address that sent the email.
- Look for misspellings of the email domain name (example@emaildomainname.com) or the name of the sender.
- Do not download any attachments or click on any links within the email until you know it is safe to do so.
- Unsure if the email is legitimate? Email the company or friend who supposedly sent you the message asking them if they sent you a message recently.
Text Message
- Is the message asking you to respond? Some text messaging services will charge you a fee for responding in a particular way.
- Does the text ask you to visit the website? Does the URL of the website look legitimate? Unlike with email, text messages cannot hide a URL behind a link’s text. Therefore, check the URL to make sure it is from the company the message claims it does.
How to Report Phishing
If you do receive a phishing email or phone call, most companies have a reporting system in place so that can track the phishing attempts that claim to be from them. Please look up the procedure for reporting a phishing attempt to the real company and provide them with the needed information on the phishing attempt. Companies will track this information to find patterns and hopefully track down these attackers.
What To Do If You Fall For It
If you feel that you have fallen for a phishing scam, immediately change whatever information you provided to the attacker and any other information that your initial information could have given them access to. For example, did the attacker potentially get your email username and password? If so, they can do a password reset on any account linked to that email account to gain access to them without knowing your password. If you are unsure what you need to change, reach out to someone you trust for help, like your grandson (who just happens to work for a web development company).
How Phishing Is Being Defeated
The number one way you can help protect yourself and others is to be vigilant and question the source whenever you are asked for information. Even with the best education in the subject, some percentage of phishing attempts will work, as we are all human and make mistakes. Therefore, technology like 2-Step Verification helps prevent phishing attempts. 2-Step Verification requires that a temporary identifier also needs to be provided along with your normal identification in order to access sensitive information.
For example, Grandma accidentally provides her email username and password to an attacker through a phishing attempt. That attacker signs into her email and determines who she banks with. They then visit her bank’s website and requests a reset password. Grandma and the attacker both receive the email to reset her banking password which the attacker quickly does and deletes this email to help prevent detection. The attacker then signs into Grandma’s bank account. However, Grandma’s bank knows Grandma will fall victim to this kind of attack and implements a 2-Step Verification by text message.
When Grandma or the attacker signs into her bank account but before they are allowed to continue onto her actual banking, they send Grandma’s phone a text message with a short and unique code that is only good for a short amount of time. Grandma will need to enter this code in order to access her banking information. Since the hacker likely does not have access to Grandma’s phone, the phishing attack, on this front at least, was thwarted. The attacker never had the chance to change her phone number to theirs to intercept the special code and therefore could not access her information.
While this solution can greatly reduce the number of successful phishing attempts, it is not fool proof and slows down the experience for the legitimate users.
Be Careful Out There
Footnote 1 - Ransomware locks your computer and files so that you cannot access it unless you provide the asked ransom to the attacker. Most of the time ransomware encrypts your files so that they cannot be accessed even if moved to a clean computer.
Vanguard Tips & Tricks
We provide helpful hints you never knew you needed for our clients. Check out "Vanguard Tips & Tricks" to learn quick and simple hacks to make managing your website easier than ever.
Phishing for Grandma
My Grandma is joining the 21st century. She has a laptop, smartphone, and even a Facebook profile. Taking that leap was big, but she is taking it in strides and becoming more connected. However, her understanding of how this technology works is limited, and therefore makes her vulnerable to the more malicious side of the internet. Grandma has been hacked, attacked with ransomware,1 and started to lose faith in her choice to become more connected online. Therefore, this article is to help you (and your Grandma) understand what a Phishing attempt/attack is, identify it as such, and avoid giving away your sensitive information.
What is Phishing?
Put your tackle box and favorite rod away, were not going fishing… for fish. Instead, phishing is angler’s equivalent for hunting down information. A fisherman is chasing after fish and uses bait to tempt the fish onto their line. With phishing, the fisherman (phisherman?) is after your personal information and is using some sort of communication that seems legitimate as their bait. Put another way, phishing is one’s attempt to get information by posing as somebody or something else. For example, you receive an email from what you think is your bank saying that your online banking username and password have expired and need to be updated. You click on the link and update your information. However, when you visit your bank’s website later that day, you noticed your credentials have not been updated. You unknowingly gave away your login information to a stranger!
Phishing Mediums
While most phishing attempts are made over email, any method of communication can be exploited for the purposes of phishing information. One common theme of all phishing attempts is continued anonymity of the person phishing for information. If you can trace back where the attacker is, it would be much easier to rectify any wrongs committed. Therefore, many phishing attacks use temporary email domains or exploit a hacked website as a base of their attack.
Unfortunately, Grandma fell victim to a phishing attack by phone a couple of times. In one such instance, someone claiming they were from Microsoft, said that they detected a virus on her computer. In the course of two hours of speaking with Grandma this person was able to get her to provide them with the information necessary to access her computer remotely (using the same software I use to assist her). It was only after they had access did she become suspicious and call me for help. Unfortunately, the damage was done, and the attacker installed rudimentary ransomware1 onto her computer. We traced the phone number to an offshore “IT Support” company who, for a monthly subscription, will clean up any viruses on (and unlock any ransomware that they installed onto) your computer. Luckily, we were able to recover her files through other means, and the real loser in the scenario was the attacker who had to play the role of “tech support” to Grandma for over two hours.
How to spot
Phone calls
- Ask the caller for their name and position. Look up the support line for company they claim to be with. Hang up with the person who called you and attempt to call them back on the number you found. Do not trust any phone numbers that they provide you.
Websites
- Check the URL address of the website you are visiting for misspellings. If you are unsure, search for the website using your favorite search engine. Phishing attempts often involve buying a domain name that is similar to the real domain you are trying to visit in hopes that you don’t notice the change.
- Make sure your connection with the website is private and encrypted. Look in the upper left-corner of the URL bar for a lock icon. If your browser ever warns you that a website’s “Certificate is Self-Signed”, do not trust the website.

Emails
- Check the email address that sent you the message. This may not be the name of the individual that sent you the email. Phishing attempts often will use a friend’s name to make you think it is your friend who sent you an email. While they can spoof the name, it is much harder to spoof the email address that sent the email.
- Look for misspellings of the email domain name (example@emaildomainname.com) or the name of the sender.
- Do not download any attachments or click on any links within the email until you know it is safe to do so.
- Unsure if the email is legitimate? Email the company or friend who supposedly sent you the message asking them if they sent you a message recently.
Text Message
- Is the message asking you to respond? Some text messaging services will charge you a fee for responding in a particular way.
- Does the text ask you to visit the website? Does the URL of the website look legitimate? Unlike with email, text messages cannot hide a URL behind a link’s text. Therefore, check the URL to make sure it is from the company the message claims it does.
How to Report Phishing
If you do receive a phishing email or phone call, most companies have a reporting system in place so that can track the phishing attempts that claim to be from them. Please look up the procedure for reporting a phishing attempt to the real company and provide them with the needed information on the phishing attempt. Companies will track this information to find patterns and hopefully track down these attackers.
What To Do If You Fall For It
If you feel that you have fallen for a phishing scam, immediately change whatever information you provided to the attacker and any other information that your initial information could have given them access to. For example, did the attacker potentially get your email username and password? If so, they can do a password reset on any account linked to that email account to gain access to them without knowing your password. If you are unsure what you need to change, reach out to someone you trust for help, like your grandson (who just happens to work for a web development company).
How Phishing Is Being Defeated
The number one way you can help protect yourself and others is to be vigilant and question the source whenever you are asked for information. Even with the best education in the subject, some percentage of phishing attempts will work, as we are all human and make mistakes. Therefore, technology like 2-Step Verification helps prevent phishing attempts. 2-Step Verification requires that a temporary identifier also needs to be provided along with your normal identification in order to access sensitive information.
For example, Grandma accidentally provides her email username and password to an attacker through a phishing attempt. That attacker signs into her email and determines who she banks with. They then visit her bank’s website and requests a reset password. Grandma and the attacker both receive the email to reset her banking password which the attacker quickly does and deletes this email to help prevent detection. The attacker then signs into Grandma’s bank account. However, Grandma’s bank knows Grandma will fall victim to this kind of attack and implements a 2-Step Verification by text message.
When Grandma or the attacker signs into her bank account but before they are allowed to continue onto her actual banking, they send Grandma’s phone a text message with a short and unique code that is only good for a short amount of time. Grandma will need to enter this code in order to access her banking information. Since the hacker likely does not have access to Grandma’s phone, the phishing attack, on this front at least, was thwarted. The attacker never had the chance to change her phone number to theirs to intercept the special code and therefore could not access her information.
While this solution can greatly reduce the number of successful phishing attempts, it is not fool proof and slows down the experience for the legitimate users.
Be Careful Out There
Footnote 1 - Ransomware locks your computer and files so that you cannot access it unless you provide the asked ransom to the attacker. Most of the time ransomware encrypts your files so that they cannot be accessed even if moved to a clean computer.
Case Studies
Vanguard conducts thorough preliminary investigative work to ensure your website is built to cater specifically to your target audience and meet your organization’s goals. Check out some of the case studies on some of our most recent client success stories.
What Can Vanguard Do For You?
As your organization grows and evolves, your website should as well. Whether you are looking to generate more traffic, implement custom functionality, mobile compatibility, integrate your systems, or give your site a complete redesign, Vanguard Technology is your go-to web partner. Reach out to us with your current concerns with your website, and our experts will happily provide a solution.










Leave a commentOrder by
Newest on top Oldest on top